Project
Iris-Based Cryptography
Experimental evaluation of a biometric–cryptographic system based on iris recognition, with the goal of improving the stability and reliability of biometric keys for secure authentication.
The work addresses one of the main limitations of biometric systems: the natural variability of biometric data across different acquisitions, which can lead to authentication errors even for legitimate users.
The proposed approach combines biometric recognition and cryptographic key binding, leveraging the uniqueness and permanence of the human iris while integrating cryptographic techniques to protect sensitive data. Instead of directly using biometric templates for authentication or key generation, the system applies a Biometric/Cryptographic Key Binding technique based on function minimization, in which cryptographic keys are securely bound to biometric features through a mathematical optimization process.
The thesis begins with an in-depth analysis of biometric systems, focusing on the properties required for effective biometric authentication and motivating the choice of the iris as the primary biometric trait. The iris is shown to be particularly suitable due to its high uniqueness, long-term stability, and resistance to forgery. The work then explores traditional biometric pipelines, including acquisition, preprocessing, feature extraction, and matching, and highlights their vulnerabilities when biometric data is affected by noise and acquisition errors.
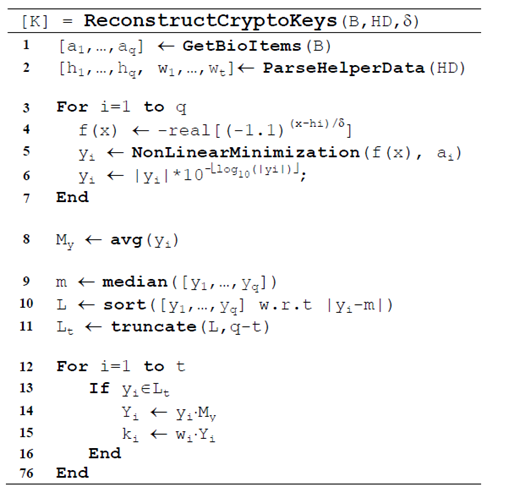
The core contribution of the thesis lies in reformulating the biometric–cryptographic binding process as a non-linear function minimization problem. Biometric and cryptographic keys are partitioned into smaller components, each associated with local minima of specially designed objective functions. Only when a biometric sample is sufficiently close to the original enrolled data does the minimization process converge to the correct set of local minima, allowing the reconstruction of the cryptographic key. This mechanism ensures both information hiding and resistance to key reconstruction attacks.
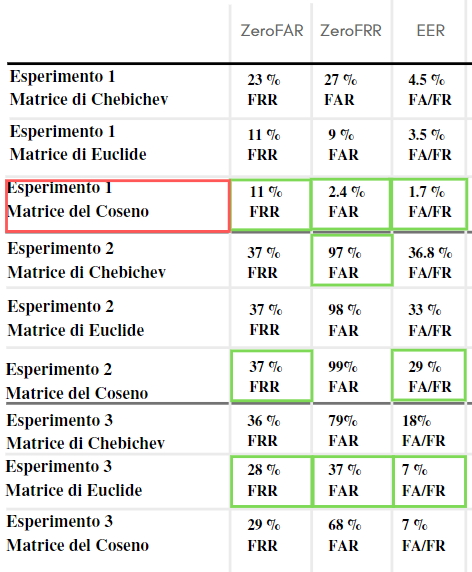
An extensive experimental evaluation is conducted using a publicly available infrared iris dataset (CASIA-IrisV2). Multiple experiments analyze the behavior of biometric distances, the impact of different similarity metrics (Chebyshev, Euclidean, and cosine distances), and the trade-offs between False Acceptance Rate (FAR) and False Rejection Rate (FRR). ROC curves and Equal Error Rate (EER) metrics are used to assess system performance under varying thresholds.
Further experiments investigate whether the binding and reconstruction process can be used not only for cryptographic key protection but also as a method for biometric key stabilization. Results show that while the approach can significantly reduce noise for very similar biometric samples, it may also introduce instability when biometric variations exceed a certain threshold, highlighting the delicate balance between robustness and security in biometric systems.
Use arrows to browse media